In today’s digital landscape, cybersecurity is not just a concern for large corporations; Small to Medium Businesses (SMBs) are increasingly prime targets for cyberattacks. One of the most effective defences against unauthorised access is Multi-Factor Authentication (MFA). But what is MFA, and why is it so critical for your business’s security? As of 2025, relying solely on passwords is no longer sufficient. Implementing MFA is a fundamental step towards securing your valuable business data, protecting client information, and ensuring operational continuity. This guide explains why your business needs MFA and explores the core concepts behind this vital security layer.
What is Multi-Factor Authentication (MFA)?

Multi-Factor Authentication (often shortened to MFA, and sometimes referred to as two-factor authentication or 2FA when exactly two factors are used) is a security process that requires users to provide two or more different verification factors to gain access to an account, application, or system. Instead of just asking for a username and password (something the user knows), MFA demands additional proof of identity from different categories of credentials. This layered approach significantly increases the difficulty for unauthorised individuals to gain access, even if they manage to steal a password, a common attack vector highlighted by numerous data breach reports.
The Core Factors of Authentication
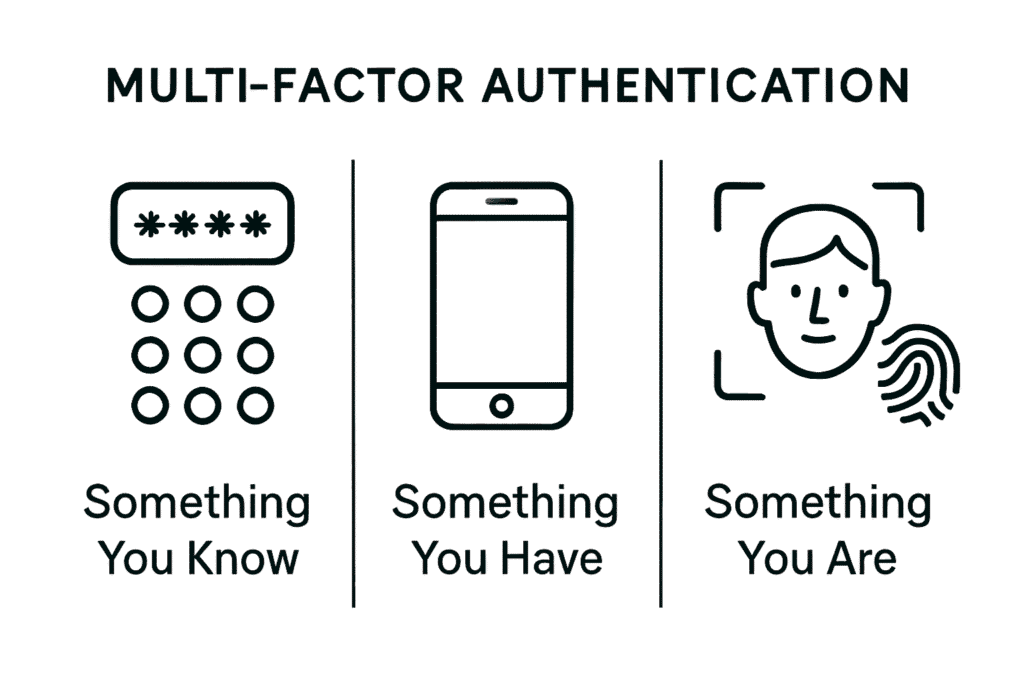
MFA relies on combining credentials from at least two of these three distinct categories:
1. Knowledge Factor (Something You Know): This is the most common factor – typically a password, PIN, or the answer to a security question. While essential, passwords alone are vulnerable to guessing, phishing, and theft.
2. Possession Factor (Something You Have): This requires proving possession of a specific physical item. Examples relevant to businesses include:
- Authenticator Apps: Mobile apps (like Google Authenticator, Microsoft Authenticator, Authy) that generate time-sensitive codes on a registered smartphone.
- SMS/Email Codes: One-time codes sent via text message or email to a registered device/account (though generally considered less secure than authenticator apps).
- Hardware Tokens: Small physical devices (like YubiKeys) that generate codes or respond to prompts when plugged in or tapped.
3. Inherence Factor (Something You Are): This uses unique biological traits for verification. Common examples include:
- Fingerprint Scans: Using built-in scanners on laptops or smartphones.
- Facial Recognition: Using device cameras for identity verification (e.g., Windows Hello, Apple Face ID).
- Voice Recognition: Less common, but uses unique vocal patterns.
True MFA requires combining factors from different categories. Using a password and a PIN (both knowledge factors) is not MFA.
Why is MFA Non-Negotiable for Small to Medium Businesses?
The statistics are stark: a significant percentage of cyberattacks leverage compromised credentials. SMBs often mistakenly believe they are too small to be targets, yet they are frequently attacked precisely because cybercriminals perceive them as having weaker defences than larger enterprises. Implementing MFA provides substantial benefits:
- Drastically Reduced Risk of Unauthorised Access: Even if a password is stolen or guessed, MFA prevents access without the additional factor(s). This is crucial for protecting sensitive business data, financial accounts, and client information.
- Enhanced Data Protection & Compliance: Many industry regulations and data privacy laws (like the Australian Privacy Principles under the Privacy Act) emphasise the need for reasonable security measures. MFA is increasingly seen as a baseline requirement for protecting personal and sensitive information.
- Increased Client and Partner Trust: Demonstrating strong security practices, including MFA, builds confidence with clients, suppliers, and partners, showing that you take data protection seriously.
- Support for Secure Remote Access: With flexible work arrangements common, MFA provides a vital security layer for employees accessing business systems and data from various locations.
- Mitigation Against Phishing & Credential Stuffing: MFA renders stolen passwords obtained through phishing attacks or reused from other breaches far less effective.
Common MFA Methods for Businesses
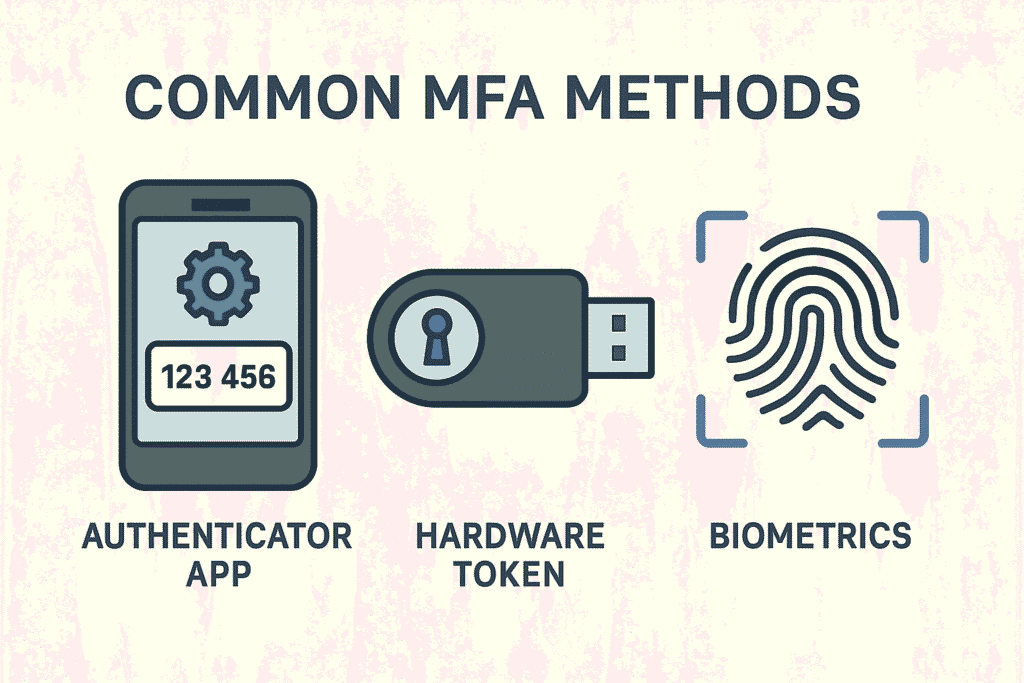
Several MFA methods are practical for businesses:
- Authenticator Apps: Widely considered a secure and convenient option. Employees install an app on their smartphone, link it to their accounts, and use the generated codes when logging in.
- Hardware Tokens (e.g., YubiKey): Offer very high security as they require physical possession and are resistant to phishing. Suitable for key personnel or highly sensitive accounts.
- Biometrics: Increasingly integrated into devices, offering convenience, though businesses need policies regarding their use and management.
- SMS/Email Codes: Easy to implement but vulnerable to SIM swapping attacks and email account compromise. Often better than no MFA, but should ideally be replaced or supplemented by stronger methods.
Implementing Multi-Factor Authentication in Your Business
Getting started with MFA involves several steps:
- Identify Critical Systems: Determine which accounts and systems hold sensitive data or provide critical access (e.g., email, financial software, CRM, cloud storage, VPN).
- Choose Appropriate MFA Methods: Select methods that balance security needs with user convenience and your IT capabilities. Authenticator apps are often a good starting point.
- Select and Configure MFA Solutions: Many platforms (Microsoft 365, Google Workspace, Xero, etc.) have built-in MFA options. Configure these according to vendor instructions.
- Develop Clear Policies: Document which systems require MFA and the approved methods.
- Train Your Staff: Educate employees on why MFA is important and how to set up and use the chosen methods correctly. Provide support during rollout.
- Monitor and Review: Regularly review MFA usage and ensure policies remain effective.
Secure Your Business Future with MFA
In conclusion, Multi-Factor Authentication is no longer an optional extra; it is an essential security control for any modern business. By adding extra layers of verification beyond a simple password, MFA significantly strengthens your defences against unauthorised access, protects critical data, aids compliance, and builds trust.
Take proactive steps today to implement MFA across your critical business systems. It is a cost-effective measure that delivers a substantial return in terms of risk reduction and peace of mind.

