Cybersecurity Services
We protect businesses from evolving cyber threats with tailored security strategies. Our experts assess risks, strengthen defenses, and ensure compliance. From endpoint protection to threat detection and response, we secure your digital assets and data. With proactive monitoring and best-in-class tools, we help you stay resilient, reduce downtime, and safeguard trust.
of cyberattacks target small and medium-sized businesses.
of small businesses close within 6 months of a major cyber breach.
is the global average cost of a data breach, covering lost business, legal fees, and recovery.
of malware is delivered via email, making phishing the top threat vector.
CYBERSECURITY PROTECTION
Cybersecurity process to safeguard your business from evolving digital threats.
Technical
We strengthen defenses to protect your networks, systems, and apps from breaches and vulnerabilities.
Monitoring
We constantly watch for suspicious activity so threats are caught early—before they become incidents.
Response
We act fast to contain risks and recover smoothly, minimizing downtime and protecting your reputation.
Why Choose Us
What Sets Us Apart
Proactive Threat Intelligence
We stay ahead of cyber threats with real-time monitoring and predictive insights.
Risk Management & Compliance
We balance security with compliance to meet industry standards.
Adaptive Defense Strategies
Our defense strategies evolve with emerging threats, keeping you secure at all times.
Building Resilience Through Education
We foster a culture of security by continuously educating your team on best practices.




















CYBERSECURITY FAQ
Answers to common questions about cybersecurity
What is cybersecurity and why is it important for my business?
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks. It’s crucial for businesses of all sizes to prevent data breaches, financial losses, reputational damage, and regulatory penalties.
What types of cybersecurity services do you offer?
We offer a range of services including:
- Network Security
- Endpoint Protection
- Penetration Testing
- Vulnerability Assessments
- Managed Detection and Response (MDR)
- Security Awareness Training
- Incident Response and Recovery
How do I know if my organization is vulnerable to cyber threats?
Common signs include outdated software, lack of multi-factor authentication, no cybersecurity policy, or previous incidents. A security assessment or vulnerability scan can provide a clear picture.
What is a penetration test and do I need one?
A penetration test (pen test) simulates a cyberattack on your systems to identify weaknesses before attackers do. If your company handles sensitive data or must comply with standards like PCI-DSS or ISO 27001, regular pen tests are essential.
How often should we conduct a cybersecurity audit or assessment?
At minimum, annually. However, more frequent assessments (quarterly or after major changes) are recommended for high-risk or highly regulated environments.
Do you offer cybersecurity services for small businesses?
Yes. Our services are scalable and tailored to fit businesses of all sizes. Cybercriminals often target small businesses due to perceived weaker defenses.
What should I do if I think I’ve been hacked?
Act quickly:
- Disconnect affected systems from the internet.
- Avoid tampering with evidence.
- Contact your internal IT team and/or a cybersecurity incident response provider (like us).
- Notify relevant stakeholders as required.
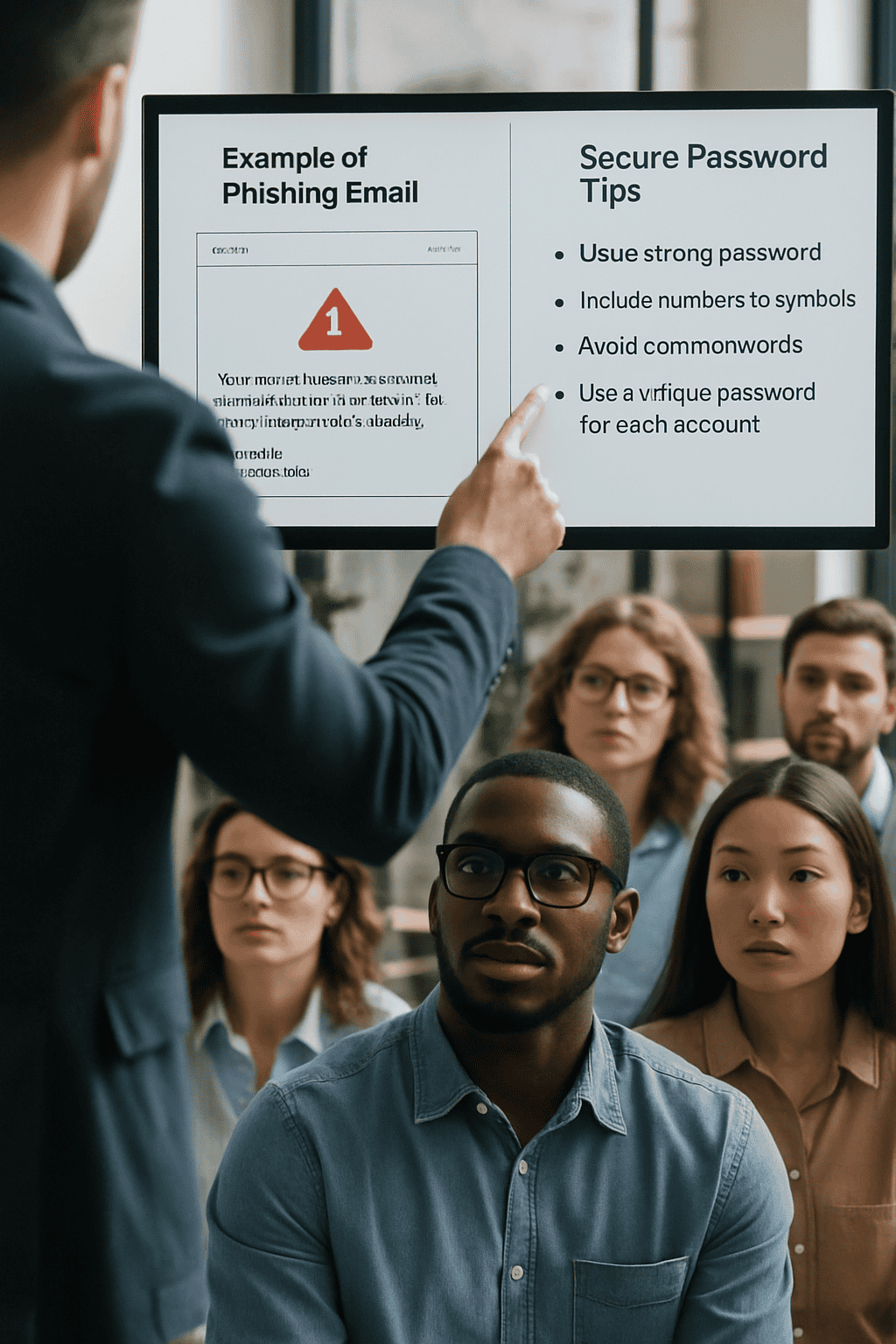
How can I train my staff to recognize cyber threats?
We provide cybersecurity awareness training that covers phishing, social engineering, secure password practices, and more—customized to your industry and risk level.
How much do your cybersecurity services cost?
Costs vary depending on the scope and complexity of your needs. We offer flexible pricing models including one-time audits, project-based engagements, and monthly retainers.
Can you help us after a cyber incident has occurred?
Absolutely. Our incident response team can help contain, investigate, and recover from cyberattacks. We also assist with forensics and post-incident reviews.
What makes your cybersecurity services different?
We combine deep technical expertise, tailored service plans, and a proactive approach to help you stay ahead of evolving cyber threats.
Cybersecurity Powered by Leading Brands
Leveraging industry-leading brands to secure your business.






Testimonials
What Our Clients Say About Us
Ready to strengthen your cybersecurity posture?
Reach out today to learn how our expert cybersecurity solutions can help protect your business from evolving threats, ensure compliance, and keep your data and systems secure.
