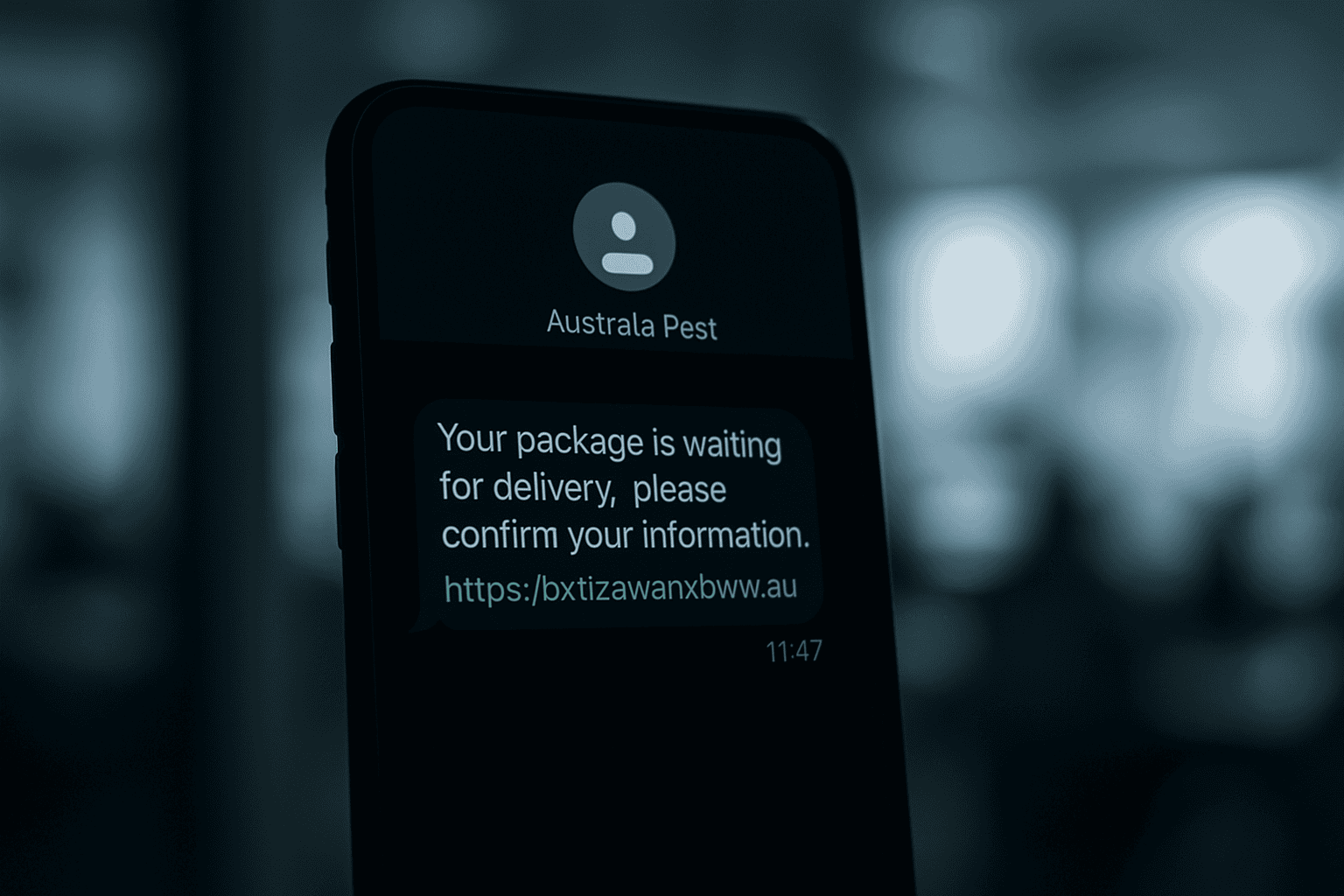
In an increasingly digital world, the threat of cybercrime looms large for businesses of all sizes. One of the most pervasive and deceptive threats currently targeting Australian businesses is the Australia Post scam texts. These fraudulent messages, expertly crafted to mimic legitimate communications from Australia Post, are designed to trick your employees into divulging sensitive information, leading to potentially devastating financial and reputational consequences.
This guide provides a comprehensive overview of Australia Post scam texts. We will explore how these scams work, the red flags to watch out for, the potential impact on your business, and, most importantly, the proactive steps you can take to protect your organisation and train your team to become a human firewall against these malicious attacks.
How Australia Post Scam Texts Work
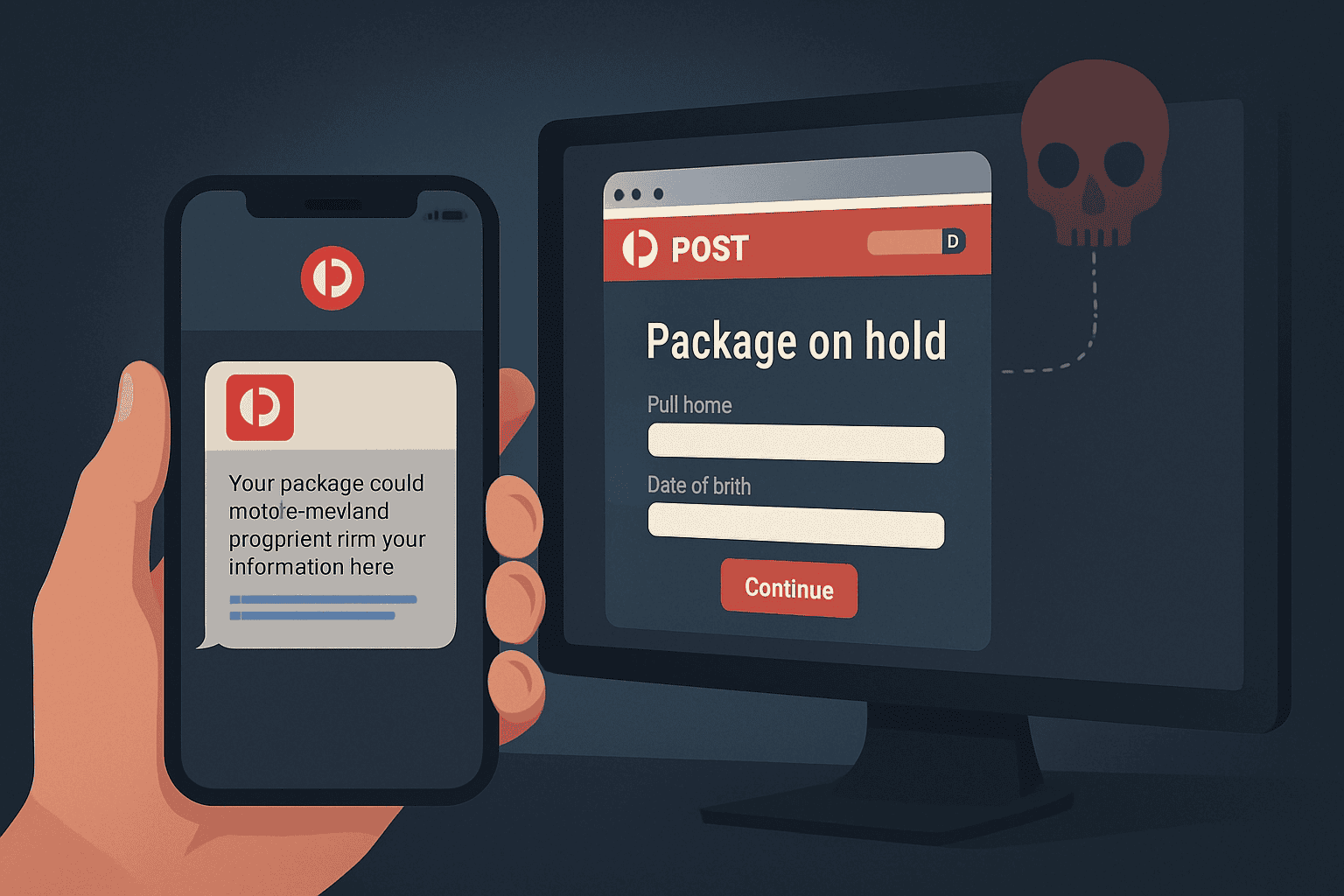
Australia Post scam texts operate on a simple yet effective premise: they exploit the trust that people have in one of Australia’s most recognised and essential services. Scammers send text messages that appear to be from Australia Post, typically regarding a parcel delivery or a missed package. These messages often contain a link that, when clicked, leads to a fake Australia Post website or a phishing site designed to steal personal and financial information.
The sophistication of these scams has grown significantly. The fake websites often look remarkably similar to the official Australia Post site, making it difficult for even savvy users to spot the deception. Once on the fake site, victims may be asked to provide personal details, credit card information for a small delivery fee, or even download malicious software (malware) onto their device. This malware can then be used to steal data, compromise systems, or launch further attacks.
These scams leverage social engineering tactics, creating a sense of urgency or curiosity to prompt immediate action. The messages might claim a package is delayed, requires a small payment for redelivery, or that there’s an issue with a shipment, all designed to bypass critical thinking and encourage a quick click.
Red Flags: How to Spot Australia Post Scam Texts

Educating your employees on the tell-tale signs of an Australia Post scam text is your first and most crucial line of defence. Scammers are constantly evolving their methods, but several common red flags can help identify fraudulent messages:
- Unsolicited Messages: The most significant red flag. If an employee receives a text about a parcel they weren’t expecting, or from a sender they don’t recognise, it should immediately raise suspicion. Legitimate Australia Post communications are usually in response to an expected delivery.
- Requests for Personal or Financial Information: Australia Post will never ask for personal details, banking information, or credit card numbers via text message for delivery or redelivery. Any message requesting such information is a scam.
- Urgent or Threatening Language: Scammers often use high-pressure tactics, such as warnings about immediate package return, extra fees, or legal action, to create a sense of urgency and panic. This is designed to bypass rational thought and prompt a hasty click.
- Suspicious Links: The link in the text message is often the most direct indicator of a scam. Hovering over the link (without clicking) on a desktop or long-pressing on a mobile device might reveal a URL that does not belong to Australia Post (e.g., auspost.delivery-update.com instead of auspost.com.au). Look for misspellings, extra characters, or unusual domain extensions.
- Poor Grammar or Spelling: While some scam texts are well-written, many still contain grammatical errors, typos, or awkward phrasing. These small mistakes can be a giveaway.
- Generic Greetings: Scam messages often use generic greetings like “Dear Customer” instead of addressing the recipient by name, even if Australia Post has their details.
- Unexpected Fees: Any message demanding a small payment for redelivery or customs fees via a link in the text is highly suspicious. Legitimate fees are typically handled through official channels or upon delivery.
By training your team to recognise these red flags, you empower them to act as a critical barrier against these phishing attempts.
The Business Impact: Why Businesses Should Care
While an Australia Post scam text might seem like a minor annoyance, the consequences for a business can be severe and far-reaching. These scams are not just about individual users losing a few dollars; they represent a significant cybersecurity threat that can cripple business operations, damage reputation, and lead to substantial financial losses.
Here’s how Australia Post scam texts can impact your business:
- Data Breaches and Confidentiality Loss: The primary goal of many scam texts is to trick employees into revealing login credentials, personal information, or even sensitive company data. If an employee falls victim, it can lead to unauthorised access to business systems, customer databases, or financial records, resulting in a costly and damaging data breach.
- Financial Loss: Beyond direct theft of credit card details, successful scam attacks can lead to fraudulent transactions, ransomware infections that demand payment, or business email compromise (BEC) where scammers trick employees into making unauthorised payments to fake suppliers. These losses can be devastating for a business with limited financial reserves.
- Malware and System Compromise: Clicking on malicious links can lead to the download of malware, including viruses, spyware, or ransomware. A malware infection can spread across your business network, encrypting critical data, disrupting operations, and requiring extensive IT resources to remediate.
- Reputational Damage: If your business systems are compromised due to a scam or if customer data is exposed, your reputation can suffer irreparable harm. Customers lose trust in businesses that cannot protect their information, leading to loss of business and negative publicity.
- Operational Disruption and Downtime: Dealing with the aftermath of a successful scam attack—whether it’s recovering from a data breach, removing malware, or restoring systems—can lead to significant operational downtime. This means lost productivity, missed deadlines, and an inability to serve customers, directly impacting your bottom line.
- Legal and Regulatory Consequences: Depending on the nature of the data compromised, businesses may face legal liabilities, fines, and regulatory penalties, especially concerning data privacy laws like the Australian Privacy Act. Responding to these legal challenges adds further financial and administrative burden.
- Employee Morale and Trust: Falling victim to a scam can be a distressing experience for employees, leading to decreased morale and a sense of vulnerability. It can also erode trust within the organisation if security protocols are perceived as weak.
Understanding these potential impacts underscores the critical importance of proactive measures to protect your business from Australia Post scam texts and similar phishing attacks.
Proactive Prevention: Safeguarding Your Business from Australia Post Scam Texts
Protecting your business from Australia Post scam texts requires a multi-layered approach that combines technological safeguards with robust employee education. Implementing these proactive measures can significantly reduce your vulnerability to phishing attacks, including those targeting your organisation.
1. Employee Education and Training: Your Strongest Defence
Your employees are your first and most critical line of defence. Regular and comprehensive cybersecurity awareness training is paramount. This training should cover:
- Recognising Phishing Attempts: Teach employees to identify the red flags discussed earlier, emphasising the importance of scrutinising sender details, links, and message content.
- The Dangers of Clicking Unknown Links: Instil a “think before you click” mentality. Explain the potential consequences of clicking malicious links, including malware infections and data breaches.
- Verification Procedures: Establish clear protocols for verifying suspicious communications. Employees should know to independently verify any unexpected delivery notifications directly with Australia Post through official channels (their website, official app, or customer service number), never by clicking links in the suspicious message.
- Reporting Suspected Scams: Create a clear and easy process for employees to report suspicious emails or texts to your IT department or managed service provider (MSP). This allows for quick analysis and enables your organisation to block similar threats.
- Password Best Practices: Reinforce the importance of strong, unique passwords and the use of multi-factor authentication (MFA) for all business accounts. Even if credentials are stolen via a scam, MFA can prevent unauthorised access.
2. Implement Robust Technical Safeguards
Beyond human vigilance, technological solutions provide essential layers of protection:
- Email and SMS Filtering: Deploy advanced email and SMS filtering solutions that can detect and block known phishing attempts and malicious links before they reach your employees’ inboxes or phones. These systems use threat intelligence to identify and quarantine suspicious messages.
- Endpoint Detection and Response (EDR): Implement EDR solutions on all company devices (laptops, desktops, mobile phones). EDR can detect and respond to malicious activity, even if an employee accidentally clicks a malicious link, by isolating infected devices and preventing malware from spreading.
- Web Filtering and DNS Security: Use web filtering services that block access to known malicious websites and phishing sites. DNS (Domain Name System) security can prevent devices from connecting to fraudulent domains, even if a user clicks a bad link.
- Regular Software Updates and Patch Management: Ensure all operating systems, applications, and security software on company devices are kept up-to-date with the latest security patches. Scammers often exploit known vulnerabilities in outdated software.
- Data Backup and Recovery: Implement a robust data backup and recovery strategy. In the event of a ransomware attack or data loss due to a scam, reliable backups ensure business continuity and minimise downtime.
- Multi-Factor Authentication (MFA): Enforce MFA across all business applications and services. Even if an employee’s username and password are compromised through a phishing scam, MFA adds a layer of security, making it significantly harder for attackers to gain access.
3. Establish Clear Incident Response Procedures
Despite best efforts, a scam might occasionally succeed. Having a clear incident response plan is crucial:
- Immediate Action: Train employees on what to do immediately if they suspect they have fallen victim to a scam (e.g., disconnect from the network, change passwords, report to IT).
- Containment and Eradication: Your IT team or MSP should have procedures to contain the breach, remove any malware, and secure compromised accounts.
- Notification and Reporting: Understand your obligations for notifying affected individuals and relevant authorities (e.g., the Australian Cyber Security Centre – ACSC) in the event of a data breach.
- Post-Incident Review: Conduct a thorough review after any incident to identify weaknesses and improve your security posture.
By combining these strategies, businesses can build a resilient defence against Australia Post scam texts and protect their valuable assets.